replace token: /home/OSUSER OSUSER OSGROUP <PASSWORD> 192.168.137.56 192.168.137.1 scancentral@esvali.com
■ 테스트 환경
-로그인 계정: OSUSER:OSGROUP
-설치 디렉토리: /home/OSUSER
-Fortify SSC: 192.168.137.1
-ScanCentral Controller: 192.168.137.56
-ScanCentral Client: 192.168.137.1
-ScanCentral Sensor #1~#3: 192.168.137.57~59
■ ScanCentral 설치
1. ScanCentral Controller
⑴ 준비 작업
JRE 설치 (JRE_HOME 및 JAVA_HOME 환경변수 확인)
⑵ Fortify ScanCentral Controller 압축 해제 및 심볼릭 링크
unzip -d sctrl_2310 Fortify_ScanCentral_Controller_23.1.0_x64.zip
ln -s sctrl_2310 sctrl
⑶ config.properties 백업
cp -f /home/OSUSER/sctrl/tomcat/webapps/scancentral-ctrl/WEB-INF/classes/config.properties /home/OSUSER/sctrl/tomcat/webapps/scancentral-ctrl/WEB-INF/classes/config.properties.orig
⑷ config.properties 수정
sed -i 's/worker_auth_token=CHANGEME123!/worker_auth_token=<PASSWORD>/g' /home/OSUSER/sctrl/tomcat/webapps/scancentral-ctrl/WEB-INF/classes/config.properties
sed -i 's/client_auth_token=CHANGEME321!/client_auth_token=<PASSWORD>/g' /home/OSUSER/sctrl/tomcat/webapps/scancentral-ctrl/WEB-INF/classes/config.properties
sed -i 's/ssc_scancentral_ctrl_secret=changeme/ssc_scancentral_ctrl_secret=<PASSWORD>/g' /home/OSUSER/sctrl/tomcat/webapps/scancentral-ctrl/WEB-INF/classes/config.properties
sed -i 's/smtp_host=localhost/smtp_host=192.168.137.1/g' /home/OSUSER/sctrl/tomcat/webapps/scancentral-ctrl/WEB-INF/classes/config.properties
sed -i 's/from_email=changeme@yourcompanyname.com/from_email=scancentral@esvali.com/g' /home/OSUSER/sctrl/tomcat/webapps/scancentral-ctrl/WEB-INF/classes/config.properties
sed -i 's/ssc_url=http:\/\/localhost:8180\/ssc/ssc_url=http:\/\/192.168.137.1:8080\/ssc/g' /home/OSUSER/sctrl/tomcat/webapps/scancentral-ctrl/WEB-INF/classes/config.properties
sed -i 's/this_url=http:\/\/localhost:8080\/scancentral-ctrl/this_url=http:\/\/192.168.137.56:8080\/scancentral-ctrl/g' /home/OSUSER/sctrl/tomcat/webapps/scancentral-ctrl/WEB-INF/classes/config.properties
vi /home/OSUSER/sctrl/tomcat/webapps/scancentral-ctrl/WEB-INF/classes/config.properties
job_expiry_delay=168 (권고 값)확인
⑸ ScanCentral Controller systemd 스크립트 작성
sudo -i
chmod 755 /home/OSUSER/sctrl/tomcat/bin/*.sh
vi /usr/lib/systemd/system/sctrl.service
-----------------------------------------------------------
[Unit]
Description=Fortify ScanCentral Controller
After=network.target
[Service]
Type=forking
Environment='JAVA_HOME=/home/OSUSER/jdk-11.0.16.1'
Environment='CATALINA_PID=/home/OSUSER/sctrl/tomcat/temp/sctrl.pid'
Environment='CATALINA_HOME=/home/OSUSER/sctrl/tomcat'
Environment='CATALINA_BASE=/home/OSUSER/sctrl/tomcat'
Environment='CATALINA_OPTS=-Xms512M -Xmx2G -Xss512K -server'
Environment='JAVA_OPTS=-Djava.awt.headless=true -Djava.security.egd=file:/dev/./urandom'
WorkingDirectory=/home/OSUSER/sctrl/tomcat
ExecStart=/home/OSUSER/sctrl/tomcat/bin/startup.sh
ExecStop=/home/OSUSER/sctrl/tomcat/bin/shutdown.sh
User=OSUSER
Group=OSGROUP
UMask=0007
[Install]
WantedBy=multi-user.target
-----------------------------------------------------------
chmod 644 /usr/lib/systemd/system/sctrl.service
systemctl daemon-reload
systemctl enable sctrl.service
⑹ ScanCentral Controller 작동 확인
http://192.168.137.56:8080/scancentral-ctrl/
"Fortify ScanCentral Controller XX.X.X.XXXX" 라고 나오면 정상
2. ScanCentral Client (Embedded Client 방식으로 설치)
기존에 SCA가 설치되어 있고 기 설치되어 있는 SCA에 ScanCentral Client를 덮어 쓰는 방식으로 설치한다.
빌드 결과를 센서로 오프로딩(트래픽 분산)하는 것을 지원하는 언어를 사용하는 경우 SCA 없이 구동 가능한 독립형 클라이언트로 구축 가능
▣ 오프로딩 지원 가능한 언어
⊙ Python
⊙ Go
⊙ Ruby
⊙ JavaScript
⊙ PHP
⊙ Java
⊙ ABAP (Advanced Business Application Programming)
⊙ Apex (Salesforce)
⊙ Classic ASP (ASP Classic)
⊙ Adobe ColdFusion
⊙ PL/SQL / T-SQL
⊙ Microsoft TypeScript
⊙ Visual Basic 6.0
⊙ .NET applications (C#, VB.NET, .NET Core, ASP.NET, and .NET Standard)
⊙ Dockerfiles
⑴ Fortify ScanCentral Client 압축 해제 및 심볼릭 링크
unzip -d scli_2310 Fortify_ScanCentral_Client_23.1.0_x64.zip
ln -s scli_2310 scli
chmod 755 /home/OSUSER/scli/bin/scancentral
⑵ 설정파일에서 auth_token 설정
sed -i 's/client_auth_token=$/client_auth_token=<PASSWORD>/g' /home/OSUSER/scli/Core/config/client.properties
sed -i 's/worker_auth_token=$/worker_auth_token=<PASSWORD>/g' /home/OSUSER/scli/Core/config/worker.properties
⑶ SCA 백업
mkdir -p /home/OSUSER/sca/sca_backup/Core
cp -Rf /home/OSUSER/sca/bin /home/OSUSER/sca/sca_backup/
cp -Rf /home/OSUSER/sca/Core/lib /home/OSUSER/sca/sca_backup/Core/
cp -Rf /home/OSUSER/sca/Core/config /home/OSUSER/sca/sca_backup/Core/
⑷ ScanCentral Client 설치 (SCA 디렉토리에 파일 복사)
echo '#!/bin/sh' > tmp.sh
echo 'cp -Rfv /home/OSUSER/scli/* /home/OSUSER/sca' >> tmp.sh
chmod 755 tmp.sh
./tmp.sh
rm -f tmp.sh
3. ScanCentral Sensor
SCA가 기 설치되어 있는 환경에서 실행한다.
⑴ 설정파일에서 auth_token 설정
sed -i 's/client_auth_token=$/client_auth_token=<PASSWORD>/g' /home/OSUSER/sca/Core/config/client.properties
sed -i 's/worker_auth_token=$/worker_auth_token=<PASSWORD>/g' /home/OSUSER/sca/Core/config/worker.properties
⑵ 가동 테스트
/home/OSUSER/sca/bin/scancentral -url http://192.168.137.56:8080/scancentral-ctrl/ worker
launcher.log will be stored in "/home/OSUSER/.fortify/scancentral-23.1.0/log" directory.
Checking for updates...
No update available or auto update is disabled on the controller.
scancentral.log will be stored in "/home/OSUSER/.fortify/scancentral-23.1.0/log" directory.
Setting up SCA version...
Retrieving SCA version...
Initializing sensor authentication token...
Worker process UUID: 6827c4cb-e334-4936-a719-f4c50711f913
Worker UUID (new): 767cf783-d9f1-44ad-a128-43aa33b474cc
Pinging the Controller...
The Controller at http://192.168.137.56:8080/scancentral-ctrl is UP
The state of the Controller is ACTIVE at Mon Jul 10 22:18:43 KST 2023
Preparing SCA for work...
Ready for work.
<Ctrl+C로 테스트 중지>
⑶ ScanCentral Sensor systemd 스크립트 작성
sudo -i
vi /usr/lib/systemd/system/scsensor.service
-----------------------------------------------------------
[Unit]
Description=Fortify ScanCentral Sensor
After=network.target
[Service]
Type=simple
Environment='SCTRL_URL=http://192.168.137.56:8080/scancentral-ctrl/'
WorkingDirectory=/home/OSUSER/.fortify/scancentral
ExecStart=/home/OSUSER/sca/bin/scancentral -url ${SCTRL_URL} worker
ExecStop=/usr/bin/pkill -SIGTERM -ef scancentral
User=OSUSER
Group=OSGROUP
UMask=0007
[Install]
WantedBy=multi-user.target
-----------------------------------------------------------
chmod 644 /usr/lib/systemd/system/scsensor.service
systemctl daemon-reload
systemctl enable scsensor.service
※192.168.137.56은 ScanCentral Controller의 주소
⑷ ScanCentral Sensor 시작/종료
systemctl start scsensor.service
systemctl stop scsensor.service
4. Fortify SSC 설정
⑴ ADMINISTRATION > Configuration > ScanCentral로 이동
▷Enable ScanCentral: ☑
▷ScanCentral controller URL: http://192.168.137.56:8080/scancentral-ctrl
▷ScanCentral poll period (seconds): 120
▷SSC and ScanCentral controller shared secret: <PASSWORD>
⑵ SSC 재시작
■ ScanCentral Client 운영 과정
1. APPLICATION 생성
SSC > APPLICATIONS > +NEW APPLICATION VERSION
2. ScanCentral 인증 토큰 발급
⑴토큰 발급 방법-1
SSC > ADMINISTRATION > Users > Token Management > NEW
Token Type: ScanCentralCtrlToken
"Use the decoded token below with Fortify Static Code Analyzer applications such as Audit Workbench, IDE plugins, and utilities." 항목의 토큰 복사
※토큰은 재열람할 수 없기 때문에 복사 후 잘 저장해야 된다.
⑵토큰 발급 방법-2
fortifyclient -url http://192.168.137.1:8080/ssc -user OSUSER -password <PASSWORD> token -gettoken "ScanCentralCtrlToken"
⑶토큰 목록 열람
fortifyclient -url http://192.168.137.1:8080/ssc -user OSUSER -password <PASSWORD> listtokens
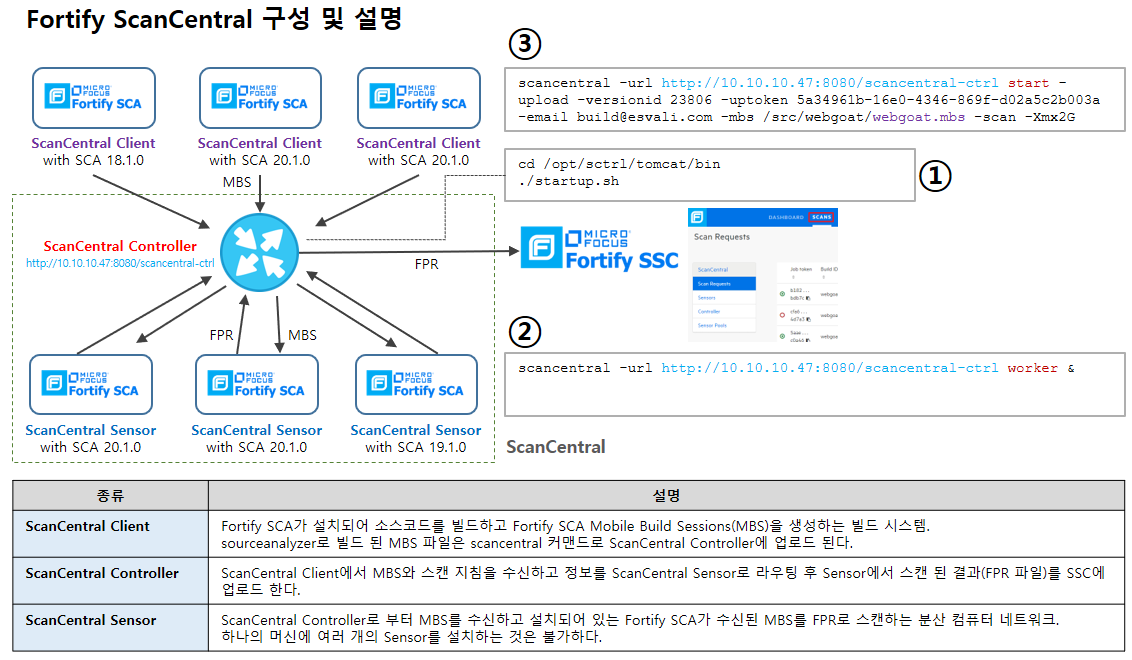
3. ScanCentral Controller에 Scan 요청
⑴ MBS 파일 생성
sourceanalyzer -b webgoat -clean
sourceanalyzer -b webgoat -source 1.5 -cp "webgoat/WebContent/WEB-INF/lib/*.jar" webgoat/JavaSource webgoat/WebContent
sourceanalyzer -b webgoat -export-build-session webgoat.mbs
sourceanalyzer -b webgoat -clean
⑵ SSC의 애플리케이션 Version ID 열람
fortifyclient -url http://192.168.137.1:8080/ssc -user OSUSER -password <PASSWORD> listApplicationVersions
⑶ 방법1: ScanCentral 서버를 통한 스캔 요청
scancentral -url http://192.168.137.56:8080/scancentral-ctrl start -upload -versionid 1 -uptoken 7f6e845a-6941-4f9f-85ea-ebad77beebde -email build@esvali.com -mbs d:\desktop\opentext_ssc_교육자료\sample\LoginProject.mbs -scan -Xmx2G
※-b <빌드명> 옵션을 통해 MBS가 아닌 빌드명으로 작업 가능하다.
※-rules 옵션을 통해 별도의 rule 파일을 지정할 수 있다. ex) -rules rule0.xml
※-filter 옵션을 통해 별도의 filter 파일을 지정할 수 있다. ex) -filter filter0.txt
※-log 옵션을 통해 로그를 지정할 수 있다. ex) -log mylog.log
※-block 옵션을 통해 스캔 작업 완료 후 FPR 파일을 서버로 다운로드가 가능하다. ex) -block -o -f webgoat0.fpr
※-scan -Xmx2G는 sourceanalyzer 옵션이다.
⑷ 방법2(구 방법): SSC를 통한 스캔 요청
scancentral -sscurl http://192.168.137.1:8080/ssc -ssctoken b712a1dc-3cd1-4167-8b38-6cdaf4b8e32a start -upload -versionid 23806 -uptoken 5a34961b-16e0-4346-869f-d02a5c2b003a -email build@esvali.com -mbs /home/OSUSER/webgoat/webgoat.mbs -scan -Xmx2G
4.ScanCentral 상태 확인 방법
SSC > SCANCENTRAL

